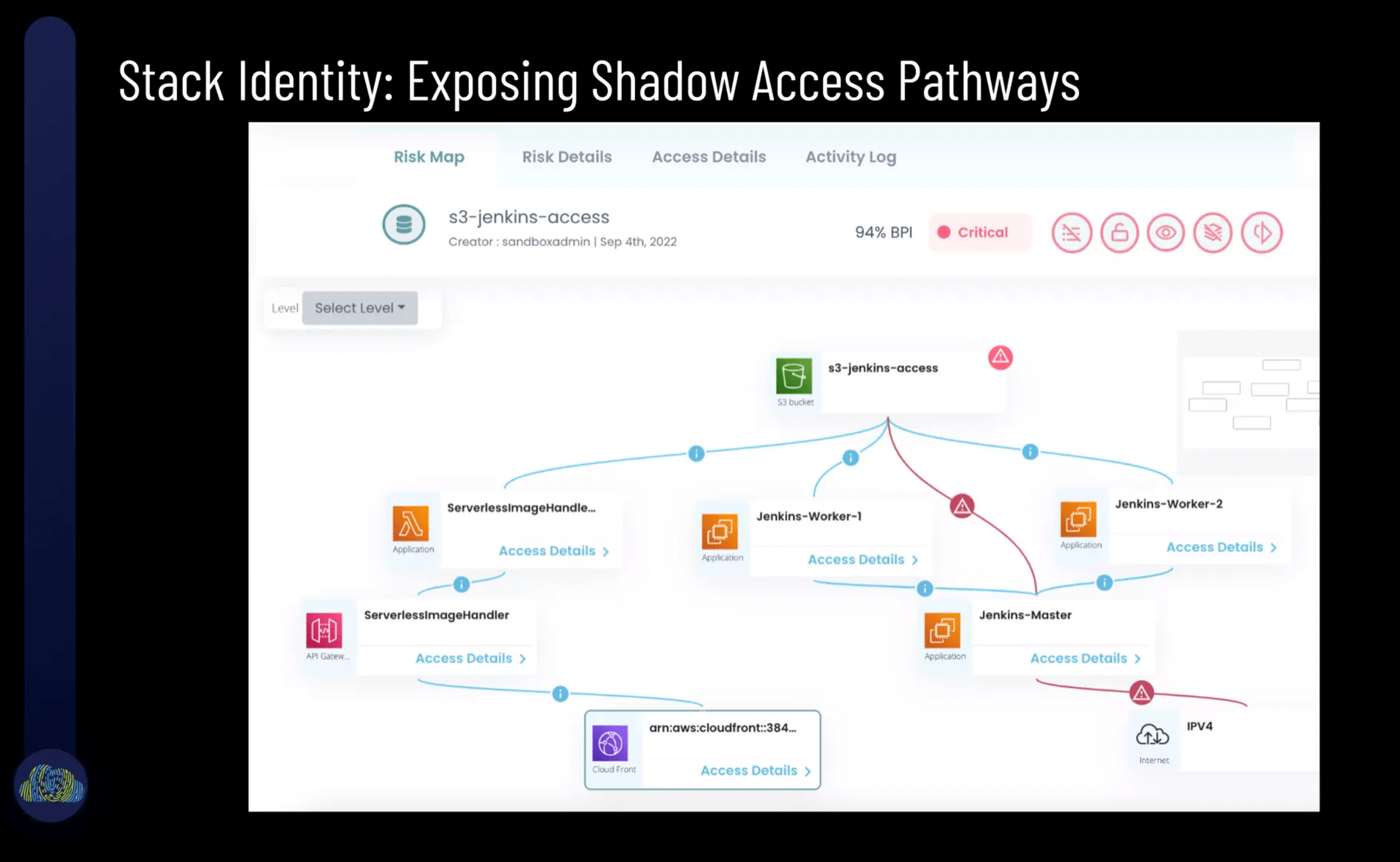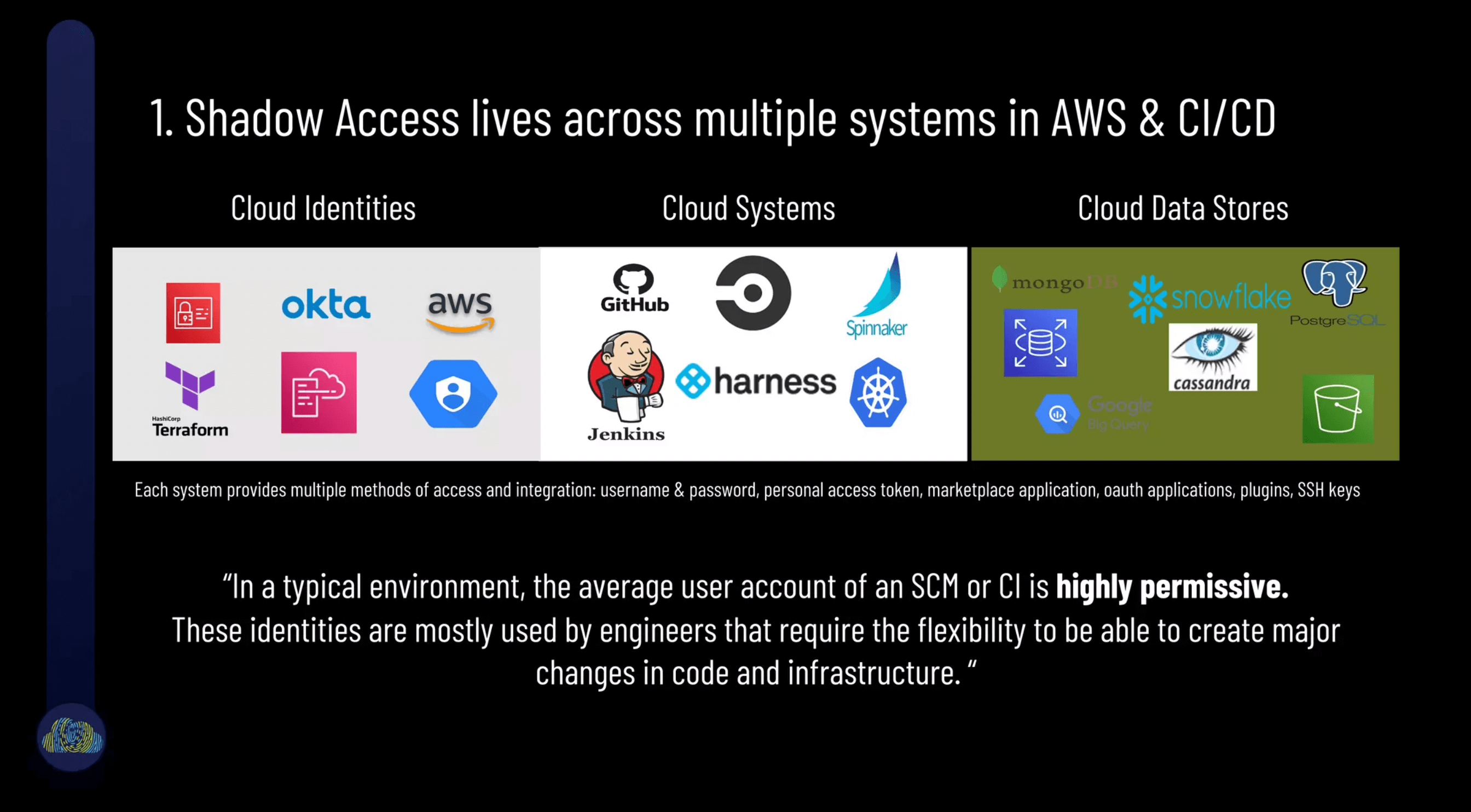
Normal cloud operations create pathways connecting different systems, apps and data that have been weaponized in almost all recent breaches.
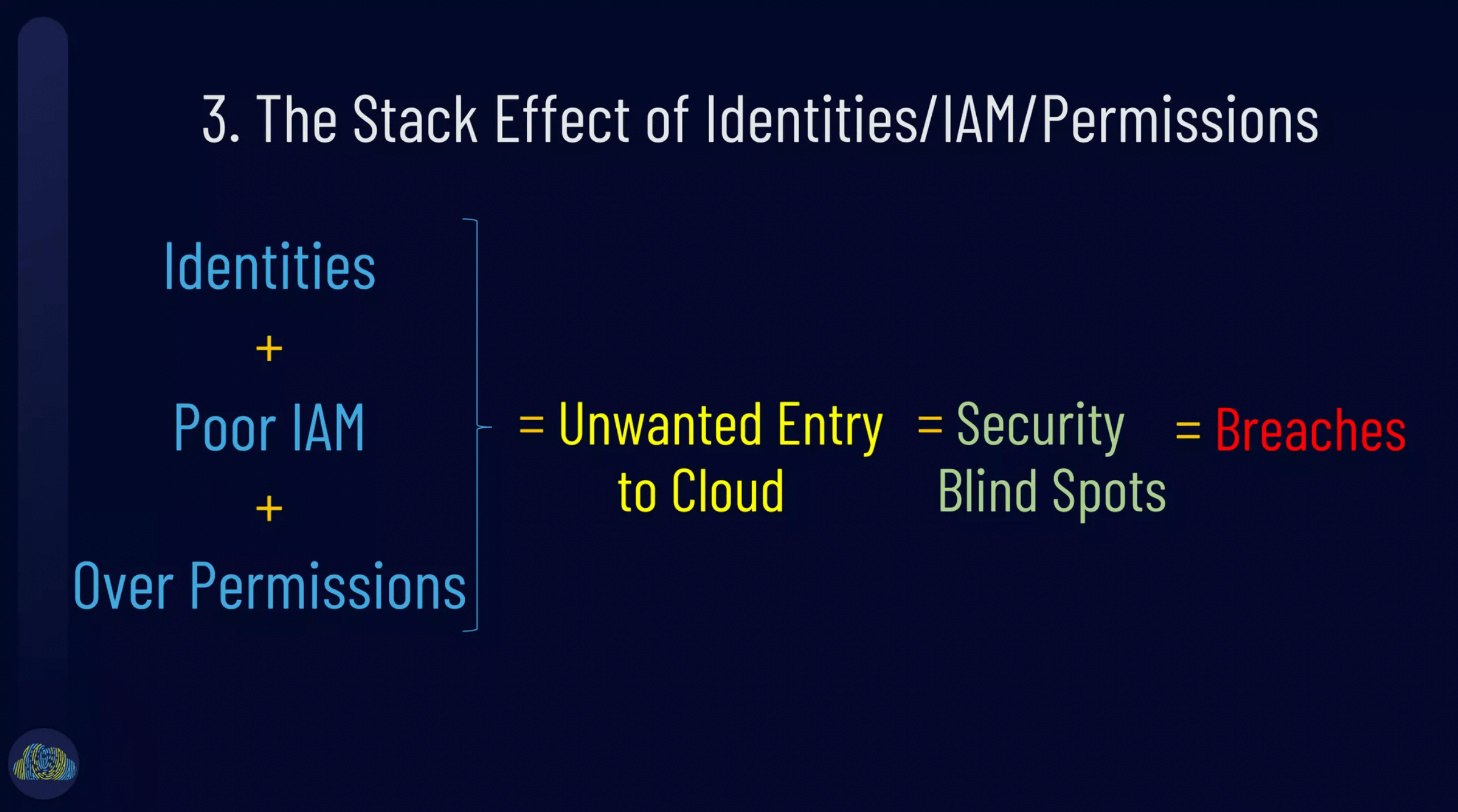
The most popular slide of the presentation was the slide depicting how shadow access attack vectors impact deployments. Different types of identities enable different access exploit vectors. These toxic combinations of identities + access vectors further combine with software supply chains and enable data access to sensitive cloud data.
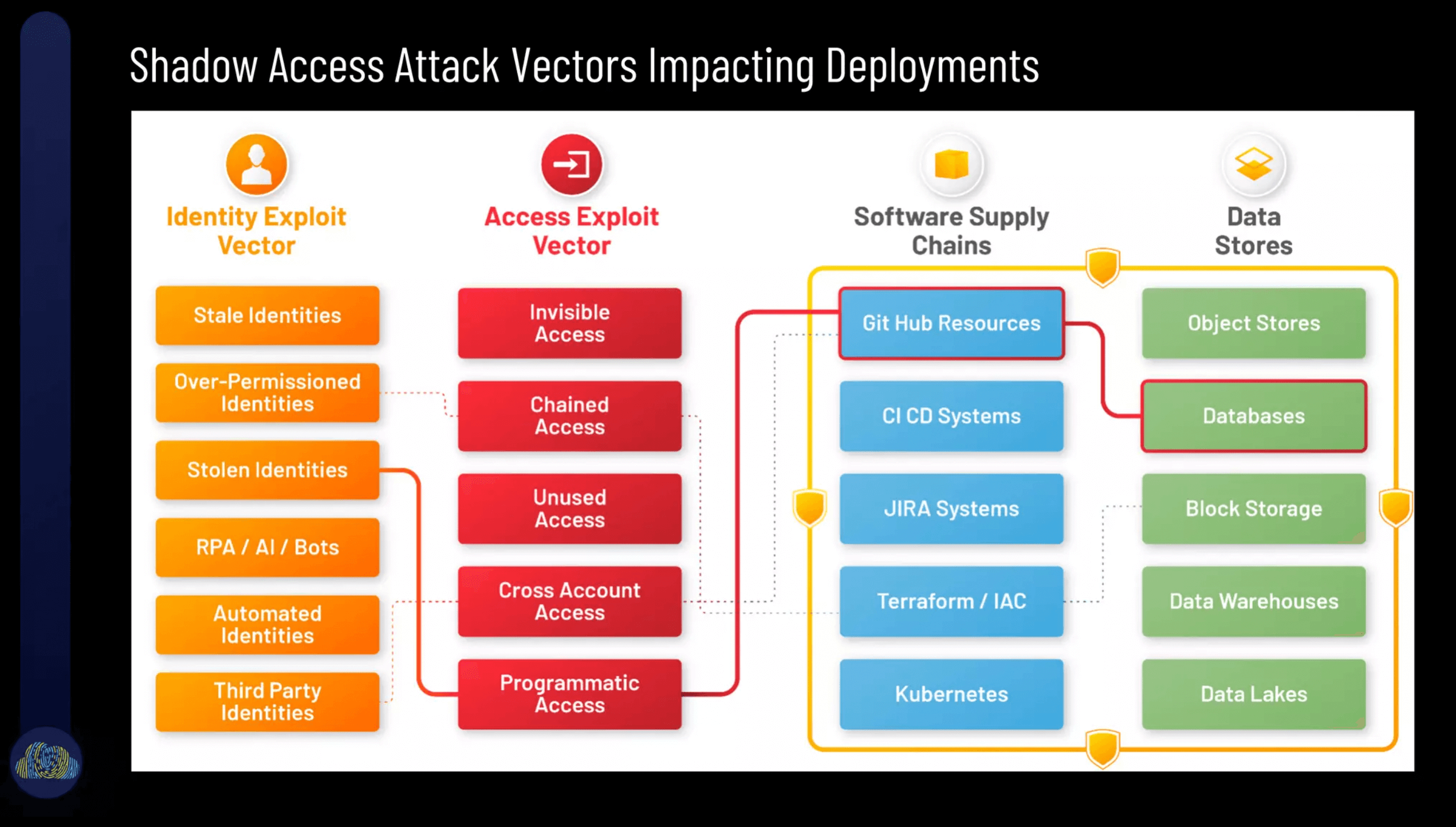
We had some good conversations with OWASP meetup attendees on the topics of chained access, access pathways and toxic combinations, and how these become part of the Top 10 CI/CD risks.

To help reduce CI/CD risks, Stack Identity provides a live data attack map that exposes these shadow pathways, revealing what are often invisible pathways that can be utilized by external attackers to exfiltrate sensitive data.